Gigabyte R133-C11 Handleiding
Lees hieronder de 📖 handleiding in het Nederlandse voor Gigabyte R133-C11 (137 pagina's) in de categorie Server. Deze handleiding was nuttig voor 33 personen en werd door 2 gebruikers gemiddeld met 4.5 sterren beoordeeld
Pagina 1/137

Gigabyte Server Management Console
User's Guide
Rev. 1.0

Copyright
© 2023 Giga Computing Technology CO., LTD. All rights reserved.
The trademarks mentioned in this manual are legally registered to their respective owners.
Disclaimer
Information in this manual is protected by copyright laws and is the property of Giga Computing.
Changes to the specications and features in this manual may be made by Giga Computing
without prior notice. No part of this manual may be reproduced, copied, translated, transmitted, or
published in any form or by any means without Giga Computing's prior written permission.
Documentation Classications
In order to assist in the use of this product, Giga Computing provides the following types of
documentation:
User Manual: detailed information & steps about the installation, conguration and use of this
product (e.g. motherboard, server barebones), covering hardware and BIOS.
User Guide: detailed information about the installation & use of an add-on hardware or
software component (e.g. BMC rmware, rail-kit) compatible with this product.
Quick Installation Guide: a short guide with visual diagrams that you can reference easily for
installation purposes of this product (e.g. motherboard, server barebones).
Please see the support section of the online product page to check the current availability of these
documents.
For More Information
For related product specications, the latest rmware and software, and other information please visit our website at
http://www.gigabyte.com/Enterprise
For GIGABYTE distributors and resellers, additional sales & marketing materials are available from our reseller
portal: http://reseller.b2b.gigabyte.com
For further technical assistance, please contact your GIGABYTE representative or visit
https://esupport.gigabyte.com/ to create a new support ticket
For any general sales or marketing enquiries, you may also message GIGABYTE server directly by email:
server.grp@gigabyte.com

- 3 -
Table of Contents
Chapter 1 Getting Started 5 ...............................................................................................
1-1 Software Requirement 5 .....................................................................................
1-2 GigabyteManagementConsoleNetworkConguration .................................. 6
1-3 Log In Gigabyte Management Console 7 ............................................................
1-3-1 Required Browser Settings: 8 ......................................................................................
1-4 Quick Button and Logged-in User 9 ....................................................................
1-5 Help ................................................................................................................ 10
1-6 Menu Bar 10 ........................................................................................................
Chapter 2 Enter Gigabyte Management Console .........................................................11
2-1 Dashboard ...................................................................................................... 11
2-2 Sensor ............................................................................................................ 12
2-2-1 Sensor Detail 13 ..........................................................................................................
2-2-2 Sensor Events 14 ........................................................................................................
2-3 System Inventory 15 ...........................................................................................
2-3-1 CPU Inventory 15 ........................................................................................................
2-3-2 DIMM Inventory 17 ......................................................................................................
2-3-3 PCI Inventory 18 ..........................................................................................................
2-3-4 HDD Inventory 19 ........................................................................................................
2-3-5 NIC Inventory 20 ..........................................................................................................
2-4 FRU Information 21 .............................................................................................
2-5 Logs & Reports 23 ..............................................................................................
2-5-1 IPMI Event Log 23 .......................................................................................................
2-5-2 System Log 24 .............................................................................................................
2-5-3 Audit Log 25 ................................................................................................................
2-5-4 Video Log 26 ...............................................................................................................
2-6 Settings .......................................................................................................... 27
2-6-1 Captured BSOD 27 ......................................................................................................
2-6-2 Date & Time ............................................................................................................28
2-6-3 External User Services 29 ...........................................................................................
2-6-4 KVM Mouse Settings 39 ..............................................................................................
2-6-5 Log Settings 40 ............................................................................................................
2-6-6 Manage Licenses 43 ...................................................................................................
2-6-7 Media Redirection Settings 43 .....................................................................................
2-6-8 Network Settings 48 ....................................................................................................
2-6-9 PAM Order Settings 56 ................................................................................................
2-6-10 Platform Event Filter 57 ...............................................................................................
2-6-11 Services ..................................................................................................................65

Getting Started - 10 -
1-5 Help
Help - The Help icon (?) is Located at the top right of the each page in Web GUI. Click this help
icontoviewmoredetailedelddescriptions.
1-6 Menu Bar
The menu bar displays the following:

- 11 -
Gigabyte Server Management Console
Chapter 2 Enter Gigabyte Management Console
2-1 Dashboard
The Dashboard page gives the overall information about the status of a device.
To open the Dashboard page, click from the menu bar. It displays the following:Dashboard
Dashboard
A brief description of the Dashboard page is given below.
Power-On Hours
It indicates the power-on time.
Pending Deassertions
It lists the all pending events incurred by various sensors and occupied/available space in logs
can be viewed. To know about the pending events details, click the More info link. This navigates
to the Event Log page.
Access Logs
A graphical representation of all events incurred by various sensors and occupied/available space
in logs can be viewed, if you click on the More info link, you can view the Audit Log page.
Today & 30 Days (Event Logs)
This page displays the list of event logs occurred by the different sensors on this device. Click
Details link on Today and 30 days to view the event logs for Today and 30 days respectively.
Sensor Monitoring
It lists all the critical sensors on the device. If you click on any list sensor, you can view the
Sensor detail page with the Sensor information and Sensor Events details.
Gigabyte Server Management Console
- 12 -
2-2 Sensor
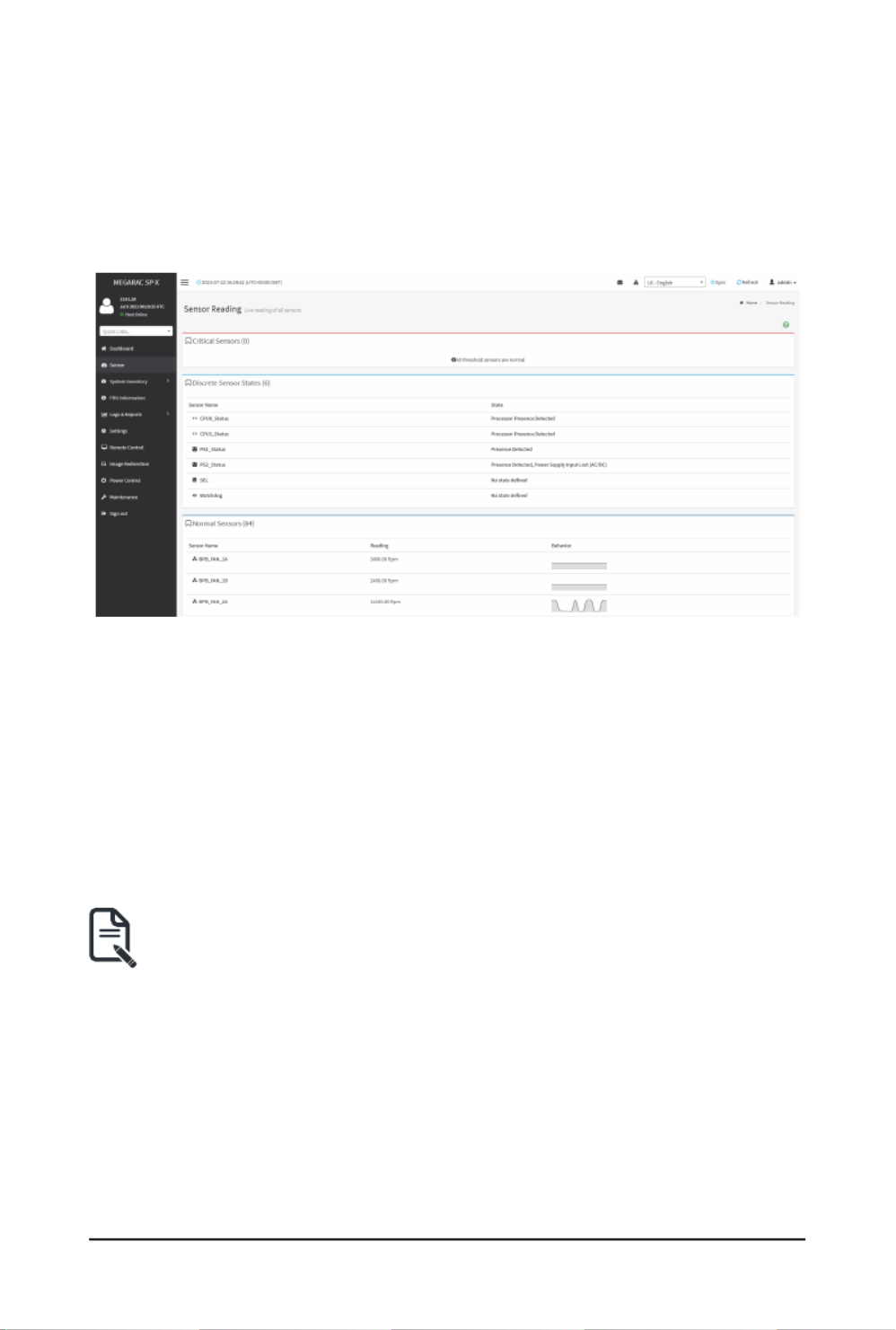
The Sensor Readings page displays all the sensor related information.
To open the Sensor Readings page, click Sensor from the menu. Click on any sensor to show
more information about that particular sensor, including thresholds and a graphical representation
of all associated events.
A sample screenshot of Sensor Readings page is shown below.
The Sensor Readings page contains the following information:
In this Sensor Reading page, Live readings for all the available sensors with details like Sensor
Name, Status, Current Reading and Behavior will be appeared, else you can choose the sensor
type that you want to display from the list. Some examples for sensors are Temperature Sensors,
Fan Sensors, Watchdog Sensors and Voltage Sensors etc.
Note: Four DIMM Temp sensors are deployed for monitoring the DIMM temperature on the
system. Users must take notice that the live reading of each DIMM Temp sensor indicates the
temperatureofaDIMMgroup,notthetemperatureofaspecicDIMM.
: Four DIMM Temp sensors are deployed for monitoring the DIMM temperature on Note
the system. Users must take notice that the live reading of each DIMM Temp sensor
indicatesthetemperatureofaDIMMgroup,notthetemperatureofaspecicDIMM.

- 13 -
Gigabyte Server Management Console
2-2-1 Sensor Detail
Select a particular sensor from the Critical Sensor or Normal Sensor lists. The Sensor Information
as Live Widget and Thresholds for the selected sensor will be displayed as shown below.
: For Illustrative Purpose, a sample screenshot of Sensor detail page with Change Note
Thresholds option is shown and explained below.
: Widgets are little gadgets, which provide real time information about a particular Note
sensor.Usercantrackasensor'sbehavioroveraspecicamountoftimeatspecic
intervals. The result will be displayed as a line graph in the widget. The session will not
expire, until the widgets gets a live data of the last widget that is kept opened.
For the selected sensor, this widget gives a dynamic representation of the readings for
the sensor.
There are six types of thresholds:
• Lower Non-Recoverable (LNR)
• Lower Critical (LC)
• Lower Non-Critical (LNC)
• Upper Non-Recoverable (UNR)
• Upper Critical (UC)
• Upper Non-Critical (UNC)
The threshold states could be Lower Non-critical - going low, Lower Non-critical - going high,
Lower Critical - going low, Lower Critical - going high, Lower Non-recoverable - going low, Lower
Non-recoverable - going high, Upper Non-critical - going low, Upper Non-critical - going high,
Upper Critical - going low, Upper Critical - going high, Upper Non-recoverable - going low, Upper
Non-recoverable - going high.
A graphical view of these events (Number of Entries vs. Thresholds) can be viewed as shown in
the Sensor Readings page screenshot.

- 15 -
Gigabyte Server Management Console
2-3 System Inventory
The System Inventory page displays the following information:
• CPU Inventory
• DIMM Inventory
• PCI Inventory
• HDD Inventory
• NIC Inventory
A screenshot displaying the menu items under System Inventory is shown below.
A detailed description of System Inventory is given below.
2-3-1 CPU Inventory
This page displays all detected CPUs on this device. Select one CPU to see the details of that
entry or click on to view all entries in details. Click DownloadExpand All SMBIOS file to
downloadtheSMBIOSle.

Gigabyte Server Management Console
- 16 -

- 17 -
Gigabyte Server Management Console
2-3-2 DIMM Inventory
This page displays all detected DIMMs on this device. It allows you to see memory attributes,
individual memory details or all entries in detail by clicking on . Click Expand All Download
SMBIOS letodownloadtheSMBIOSle.

Gigabyte Server Management Console
- 18 -
2-3-3 PCI Inventory
This page displays all detected PCI cards on this device. It allows you to see on-board PCI cards,
add-on PCI cards or all entries in detail by clicking on . Click Expand All Download SMBIOS le
todownloadtheSMBIOSle.

- 19 -
Gigabyte Server Management Console
2-3-4 HDD Inventory
This page displays all detected HDDs on this device. It allows you to see on-board HDDs, add-
on HDDs or all entries in detail by clicking on . Click Expand All Download SMBIOS file to
downloadtheSMBIOSle.

Gigabyte Server Management Console
- 20 -
2-3-5 NIC Inventory
This page displays all detected NICs on this device. It allows you to on-board NICs, add-on NICs
or all entries in detail by clicking on . Click to download the Expand All Download SMBIOS le
SMBIOSle.

- 21 -
Gigabyte Server Management Console
2-4 FRU Information
FRU Information page displays the BMC’s FRU device information. FRU page shows information
like Basic Information, Chassis Information, Board Information and Product Information of the
FRU device.
To open the FRU Information page, click from the menu bar. Select a FRU FRU Information
Device ID from the FRU Information section to view the details of the selected device. A
screenshot of FRU Information page is shown below.
Thefollowingeldsaredisplayedherefortheselecteddevice:
Available FRU Devices
• FRU device ID - Select the device ID from the drop down list
• FRU Device Name - The device name of the selected FRU device.
Chassis Information
• Chassis Information Area Format Version
• Chassis Type
• Chassis Part Number
• Chassis Serial Number
• Chassis Extra
Board Information
• Board Information Area Format Version
• Language
• Manufacture Date Time
• Board Manufacturer
• Board Product Name
• Board Serial Number
• Board Part Number
• FRU File ID
• Board Extra

Gigabyte Server Management Console
- 22 -
Product Information
• Product Information Area Format Version
• Language
• Product Manufacturer
• Product Name
• Product Part Number
• Product Version
• Product Serial Number
• Asset Tag
• FRU File ID
• Product Extra
- 23 -
Gigabyte Server Management Console
2-5 Logs & Reports
The Logs & Reports page displays the following information:
• IPMI Event Log
• System Log
• Audit Log
• Video Log
A screenshot displaying the menu items under Logs & Reports is shown below.
A detailed description of Logs & Reports is given below.
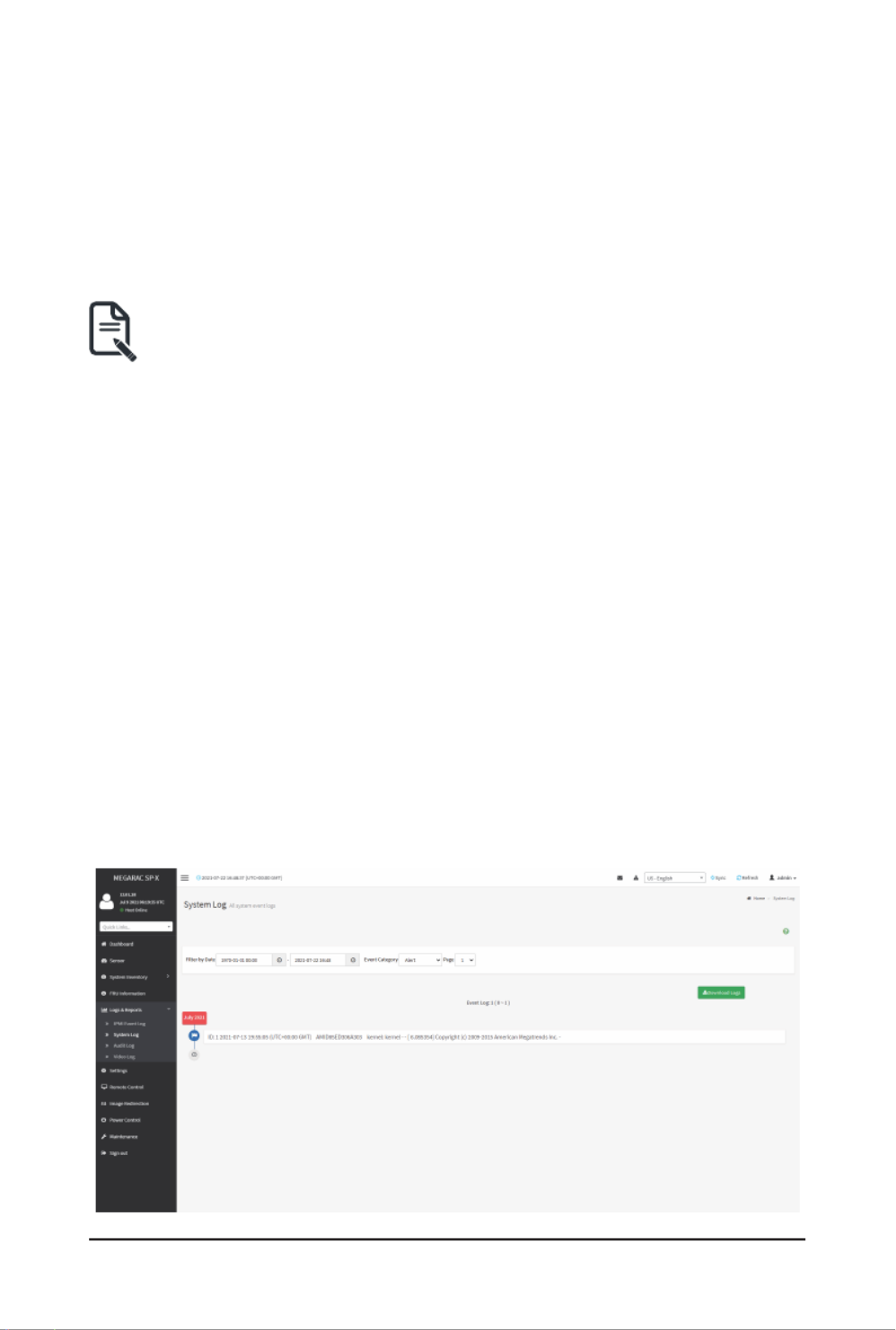
2-5-1 IPMI Event Log
This page displays the list of event logs occurred by the different sensors on this device. Double
clickonarecordtoseethedetailsofthatentry.Youcanusethesensortypeorsensornamelt
optionstoviewthosespeciceventsoryoucanalsosortthelistofentriesbyclickingonany
the column headers.
To open the Event Log page, click from the menu bar.Logs & Reports > IPMI Event Log
A sample screenshot of Event Log page is shown below.
Gigabyte Server Management Console
- 24 -
TheEventLogpageconsistsofthefollowingelds:
Filter By Date Start Date End Date: Filtering can be done by selecting and .
Filter By Type: The category could be either All Events, System Event Records, OEM Event
Records, BIOS Generated Events, SMI Handler Events, System Management Software Events,
System Software - OEM Events, Remote Console software Events, Terminal Mode Remote
Console software Events.
: Once the Filter By Date and Filter type are selected, the list of events will Note
be displayed with the Event ID, Time Stamp, Sensor Type, Sensor Name and
Description.
Event Log Statistics: Displays the statistical graph for the selected date.
Clear Event Logs: Deletes all the event logs.
Download Event Logs: Downloads the event logs.
Procedure
1. using From the Filter By Dateeld,selectthetimeperiodbyStart Date End Date and
Calendar for the event categories.
2. From the Filter By Type eld,selecttheType Sensor of the event and name to view the
events for the date. The events will be displayed based on the selected time period.
3. To clear all events from the list, click .Clear All Event Logs
4. To download the event logs, click .Download Event Logs
2-5-2 System Log
To open the System Log page, click from the menu bar.Logs & Reports > System Log
A sample screenshot of System Log page is shown below.
Note:LogsmustbeconguredunderSettings > Logs Settings > Advanced Log Settings to
display any entries. Filtering options are also available for this and all logs in this section.

- 25 -
Gigabyte Server Management Console
TheSystemLogpageconsistsofthefollowingelds:
Filter By Date Start Date End Date: Filtering can be done by selecting and .
Event Category: Filters the events you want to track based on the type of event. Options include
Alert,Critical,Error,Notication,Warning,Debug,Emergency,Information.
Download Logs: Allows you to download the system logs.
Procedure
1. using From the Filter By Dateeld,selectthetimeperiodbyStart Date End Date and
Calendar for the event categories.
2. From the Event Category eld, select the Category of the event to view the relevant
events for the dates. The events will be displayed based on the selected time period.
3. To download the event logs, click .Download Logs
2-5-3 Audit Log
To open the Audit Log page, click Logs & Reports > Audit Log from the menu bar.
A sample screenshot of Video Log page is shown below.
Note Settings > Log Settings > Advanced Log Settings:Forconguration,goto .

- 26 -
Gigabyte Server Management Console
TheAuditLogpageconsistsofthefollowingelds:
Filter By Date Start Date End Date: Filtering can be done by selecting and .
Download Logs: Allows you to download the audit logs.
Procedure
1. using From the Filter By Dateeld,selectthetimeperiodbyStart Date End Date and
Calendar for the event categories.
2. To download the event logs, click .Download Logs
2-5-4 Video Log
To open the Video Log page, click from the menu bar.Logs & Reports > Video Log
A sample screenshot of Video Log page is shown below.
Note: Video Trigger Settings should be enabled, to display the Video Log page. Video Trigger
SettingscanbeconguredunderSettings > Video Recording > Auto Video Settings > Video
Trigger Settings.
Videowillbeallowedtoplay/downloadonlyiflesizeislesserthan40MB.Browsers
have various memory restrictions, due to this browser cannot store and process data
greaterthan40MB(approximately).Iflesizeisgreaterthan40MB,userwillbenotie
with a message to use Java player Application.

Gigabyte Server Management Console
- 27 -
2-6 Settings
This group of pages allows you to access various configuration settings. A screenshot of
CongurationGroupmenuisshownbelow.
A detailed description of the Settings menu is given below.
2-6-1 Captured BSOD
This menu is used to display a snapshot of the blue screen captured at the time when/if the host
system crashed since the last reboot. A sample screenshot of Captured BSOD is shown below.
Note: KVM service should be enabled to display the BSOD. This can be configured under
Settings > Services > KVM.

- 28 -
Gigabyte Server Management Console
2-6-2 Date & Time
ThiseldisusedtosetthedateandtimeontheBMC.AsamplescreenshotofDate&Time
shown below.
TheDate&Timesectionconsistsofthefollowingelds:
Configure Date & Time: Displays Time zone list containing the UTC offset along with the
locations and Navigational line to select the location which can be used to display the exact local
time.
Automatic NTP Date & Time: Automatically synchronizes Date and Time with the NTP Server.
Primary NTP Server:Conguresaprimary NTPserver touse whenautomatically settingthe
date and time.
Secondary NTP Server:ConguresasecondaryNTPservertousewhenautomaticallysetting
the date and time.
Save:Savestheconguredsettings.
Procedure
1. Select the Time zone location from the map.
2. Enable Automatic NTP Date & Time.

Gigabyte Server Management Console
- 29 -
3. InthePrimaryNTPServer/SecondaryNTPServereld,specifytheNTPserverforth
device.
: Note SecondaryNTPserverisoptionaleld.IfthePrimaryNTPserverisnotworking
ne,thentheSecondaryNTPServerwillbeused.
4. Enable Automatic Date & Time option.
5. Click Save button to save the settings.
2-6-3 External User Services
LDAP/E-Directory Settings
The Lightweight Directory Access Protocol (LDAP)/E-Directory Settings is an application
protocol for querying and modifying data of directory services implemented in Internet Protocol (IP)
networks.
In Web GUI, LDAP is an Internet protocol that BMC can use to authenticate users. If you have
anLDAP serverconguredon yournetwork,you canuse itas an easyway toadd, manag
and authenticate BMC users. This is done by passing login requests to your LDAP Server. This
meansthatthereisnoneedtodeneanadditionalauthenticationmechanism,whenusingthe
BMC. Since your existing LDAP Server keeps an authentication centralized, you will always know
whoisaccessingthenetworkresourcesandcaneasilydenetheuserorgroup-basedpolicies
to control access.
To open External User Services page, click from the menu Settings > External User Services
bar. A sample screenshot of External User Services page is shown below.
To open LDAP/E-DIRECTORY Settings page, click Settings > External User Services > LDAP/
E-Directory Settings from the menu bar.
A sample screenshot of External User Services page is shown below.

- 30 -
Gigabyte Server Management Console
TheeldsintheLDAP/E-DirectorySettingspageareexplainedbelow.
General Settings:ConguresLDAP/E-DirectorySettings.OptionsareEnableLDAP/E-Directory
Authentication, IP Address, Port and Search base.
Role Groups: Adds a new role group to the device. Alternatively, double click on a free slot to
add a role group.
Procedure
1. In the LDAP/E-Directory Settings page, click General Settings. A sample screenshot of
General LDAP Settings page is given below.
2. Click , to enable LDAP/E-Directory Settings.Enable LDAP/E-Directory Authentication
3. Select the Encryption Type for LDAP/E-Directory.
: Note Conguretheproperportnumber,whenSSLisenabled.
4. Select the Common Name Type.

Gigabyte Server Management Console
- 31 -
5. EntertheIPaddressofLDAPserverintheServerAddresseld.
: IP Address made of 4 numbers separated by dots as in ‘xxx.xxx.xxx.xxx’.Note
Each Number ranges from 0 to 255.
First Number must not be 0.
Supports IPv4 Address format and IPv6 Address format.
CongureFQDNaddress,whenusingStartTLSwithFQDN.
6. Specify the LDAP Port in the Port eld.
: Default Port is 389.Note
For SSL connections, default port is 636.
The Port value ranges from 1 to 65535.
Port 80 is blocked for TCP/UDP protocols.
7. Specify the Bind DN that is used during bind operation, which authenticates the client to
the server.
: Bind DN is a string of 4 to 63 alpha-numeric characters.Note
It must start with an alphabetical character.
Special Symbols like dot(.), comma(,), hyphen(-), underscore(_), equal-to(=) are allowed.
Example: cn=manager, ou=login, dc=domain, dc=com
8. Enter the password in the Passwordeld.
: Password must be at least 1 character long.Note
Blank space is not allowed.
Thiseldwillnotallowmorethan47characters.
9. Enter the Search Base.TheSearchbaseallowstheLDAPservertondwhichpartof
the external directory tree to be searched. The search base may be something equivalent
to the organization or the group of external directory.
: Search base is a string of 4 to 64 alpha-numeric characters.Note
It must start with an alphabetical character.
Special Symbols like dot(.), comma(,), hyphen(-), underscore(_), equal-to(=) are allowed.
Example: ou-login, dc-domain, dc-com
10. SelectAttributeofUserLogintondtheLDAP/E-Directoryserverwhichattributesho
be used to identify the user.
: It only supports cn or uid.Note

Gigabyte Server Management Console
- 33 -
6. Select one or both of the required options
• KVM Access
• VMedia Access
7. Click to save the new role group and return to the Role Group List.Save
Active Directory Settings
An active directory is a directory structure used on Microsoft Windows based computers and
servers to store information and data about networks and domains. An active directory (sometimes
referred to as AD) does a variety of functions including the ability to provide information on
objects. It also helps to organize these objects for easy retrieval and access, allows access by
end users and administrators and allows the administrator to set security up for the directory.
ActiveDirectoryallowsyoutoconguretheActiveDirectoryServerSettings.Thedisplayedta
showsanyconguredRoleGroupsandtheavailableslots.Youcanmodify,addordeletero
groups from here. Group domain can be the AD domain or a trusted domain. Group Name should
correspond to the name of an actual AD group.
Note: To view the page, you must be at least a User and to modify or add a group, you must be
an Administrator.
To open Active Directory Settings page, click Settings > External User Settings > Active
Directory from the menu bar. A sample screenshot of Active Directory Settings page is shown
below.
TheeldsintheActiveDirectorypageareexplainedbelow.
General Settings: Configures Active Directory General Settings. Options are Enable Active
Directory Authentication, Secret User Name, Secret Password, User Domain Name, and up to
three Domain Controller Server Addresses.
Role Groups: Adds a new role group to the device. Alternatively, double click on a free slot to
add a role group.

- 34 -
Gigabyte Server Management Console
Procedure
Entering the details in General Active Directory Settings page:
1. Click on to open the General Active Directory Settings page.General Settings
2. In the Active Directory Settings page, check/uncheck the Enable Active Directory
Authentication check box to enable/disable Active Directory Authentication.
: If Active Directory Authentication is enabled, enter the required information Note
to access the Active Directory server.
3. Specify the Secret user name and password in the Secret User Name and Secret
Passwordeldsrespectively.
: Secret username/password for Active Directory is not mandatory. When secret Note
username & password is empty, Authentication fails will be always treated as Invalid
Password error.
For Invalid Password error PAM will not try other authentication methods. So it is
recommended to keep Active Directory in the last location in PAM order.
User Name is a string of 1 to 64 alpha-numeric characters.
It must start with an alphabetical character.
It is case-sensitive.
Special characters like comma, period, colon, semicolon, slash, backslash, square
brackets, angle brackets, pipe, equal, plus, asterisk, question mark, ampersand,
double quotes, space are not allowed.
Password must be at least 6 character long and will not allow more than 127 characters.
4. SpecifytheDomainNamefortheuserintheUserDomainNameeld.E.g.MyDomai
com

Gigabyte Server Management Console
- 35 -
5. CongureIPaddressesinDomain Controller Server Address 1, Domain Controller
Server Address 2 and Domain Controller Server Address 3.
: IP address of Active Directory server: At least one Domain Controller Server Note
Addressmustbecongured.IPAddressmadeof4numbersseparatedbydotsasin
“xxx.xxx.xxx.xxx”.
Each number ranges from 0 to 255.
First number must not be 0.
Domain Controller Server Addresses will supports IPv4 Address format and IPv6
Address format.
6. Click Save to the entered settings and return to Active Directory Settings page.save
Role Groups
To open Role Group page, click Settings > External User Settings > Active Directory Settings
> Role Groups from the menu bar. A sample screenshot of Role Groups page is shown below.
TheeldsintheRoleGrouppageareexplainedbelow.
Role Group Name:ThenamethatidentiestherolegroupintheActiveDirectory.
Role Group Name is a string of 64 alpha-numeric characters.Note:
Special symbols hyphen and underscore are allowed.
Group Name:ThisnameidentiestherolegroupinActiveDirectory.
Role Group Name is a string of 64 alpha-numeric characters.Note:
Special symbols hyphen and underscore are allowed.
Product specificaties
| Merk: | Gigabyte |
| Categorie: | Server |
| Model: | R133-C11 |
Heb je hulp nodig?
Als je hulp nodig hebt met Gigabyte R133-C11 stel dan hieronder een vraag en andere gebruikers zullen je antwoorden
Handleiding Server Gigabyte

1 December 2024

11 Maart 2024

11 Maart 2024

11 Maart 2024

11 Maart 2024

11 Maart 2024

11 Maart 2024

11 Maart 2024

11 Maart 2024

11 Maart 2024
Handleiding Server
- Server HP
- Server Sony
- Server Asus
- Server Medion
- Server Toshiba
- Server Abus
- Server Acer
- Server Acti
- Server Allnet
- Server Apc
- Server Asrock
- Server Axis
- Server Buffalo
- Server D-Link
- Server Dell
- Server Digi
- Server Digitus
- Server Dual Bay
- Server Eaton
- Server Elac
- Server EMC
- Server Fantec
- Server Flir
- Server Freecom
- Server Fujitsu
- Server GeoVision
- Server Hikvision
- Server Ibm
- Server In Win
- Server Iomega
- Server Kathrein
- Server LaCie
- Server Lenovo
- Server LevelOne
- Server Linksys
- Server Luxman
- Server Maxdata
- Server Megasat
- Server Monacor
- Server MSI
- Server Nec
- Server Netgear
- Server Provision ISR
- Server QNAP
- Server Quantum
- Server Revox
- Server Seagate
- Server Sitecom
- Server Sun
- Server Synology
- Server Technics
- Server Trendnet
- Server Veritas
- Server Western Digital
- Server ZyXEL
- Server Conceptronic
- Server Atlona
- Server SilverStone
- Server Intel
- Server SIIG
- Server Tripp Lite
- Server Valcom
- Server Cisco
- Server Matrox
- Server Asustor
- Server Gefen
- Server Planet
- Server Intellinet
- Server Silex
- Server Supermicro
- Server G-Technology
- Server Lindy
- Server AVerMedia
- Server Black Box
- Server Blackmagic Design
- Server ATen
- Server Extron
- Server Areca
- Server AMX
- Server SEH
- Server StarTech.com
- Server HGST
- Server Sonnet
- Server TAIDEN
- Server Advantech
- Server Moxa
- Server Smart-AVI
- Server Kramer
- Server KanexPro
- Server Avocent
- Server Teradek
- Server Vimar
- Server Hanwha
- Server Ernitec
- Server MvixUSA
- Server Promise Technology
- Server Raidsonic
- Server Rocstor
- Server Infortrend
- Server Opengear
- Server EXSYS
- Server Raritan
- Server Chenbro Micom
- Server Middle Atlantic
- Server Mr. Signal
- Server Atlantis Land
- Server C2G
- Server Lantronix
- Server IStarUSA
- Server NETSCOUT
- Server Mobotix
- Server Origin Storage
Nieuwste handleidingen voor Server

2 April 2025

2 April 2025

28 Maart 2025

28 Maart 2025

28 Maart 2025

10 Maart 2025

10 Maart 2025

10 Maart 2025

10 Maart 2025

10 Maart 2025